Another year, another slew of cyberattacks in the news — and 2021 was a doozy. According to Check Point, there was a 50% increase in attacks per week on corporate networks compared to 2020. And if your business falls victim, the results can be financially and emotionally devastating.
As we’ve said many times, prevention is better than fallout and recovery. To help you stop a cyberattack before it starts, here’s a rundown of both time-tested tools and the latest security methods.
Why can’t cyberattacks be stopped once and for all?
While the modern internet has only existed for a few decades, the concept of hacking is anything but new. Criminals have sought to exploit electronic communications since their rudimentary days. In fact, the first instance dates way back to 1834 when the French Telegraph System was compromised and financial market information was stolen.
In the nearly 200 years since, we’ve seen attacks on telephone switchboards, emulations of dial tones to place free long-distance calls, punch card tricks to obtain computer passwords, the advent of the computer virus… the list goes on.
The point? Opportunities for crime might change, but the intentions of bad actors never do. And as technology has evolved, so have criminals and their methods.
Today, network environments are more vulnerable to cyberattack than ever. With increased levels of telecommuting, many remote users are no longer behind corporate firewalls (a phenomenon called borderless business). Advances in technology create new venues for cybercrime. And of course, bad actors leverage their skills to find the new opportunities these changes bring.
Thankfully, cybersecurity professionals have kept pace. It’s important for businesses to follow suit.
What has worked so far?
Many companies have successfully leveraged the traditional methods to prevent cyberattacks. You have the long-known standard of a strong firewall with advanced threat management. Antivirus and End-Point detection and response systems on each computer and server also help keep viruses, ransomware and other malicious applications at bay.
However, it’s the human element that makes the biggest difference. That’s where IT professionals and sound procedures come into play. The highest quality hardware and software won’t help if it’s not subject to routine and thorough maintenance. Policies like the Principle of Least Privilege reduce the number of users with access to secure areas of your network to only those who truly need it. Regular security log audits help detect threats at their earliest stages. And strong data backups allow you to recover lost information more quickly should a hacker get through.
That said, the cyberattack buck doesn’t stop with your IT department. Employees at all levels have become targets of email phishing and other data-seeking tactics. This is due in part to their willingness to help and their lack of understanding about these threats. Thankfully, we’ve noticed an uptick in businesses that conduct annual user security training to help spot these and other attacks.
Isn’t that enough?
In a word: no. Bad actors often manage to find a way through these defenses. While that doesn’t mean they’re useless, they should be reinforced with modern, more advanced methods to prevent a cyberattack.
Continuous user education and training – Think of the last time you learned something… and then promptly forgot it. That’s what happens when you limit employee cybersecurity training to once per year. When you don’t put what you learn into practice, the knowledge is easily lost.
However, the bigger reason for continuous training is the speed at which new threats develop. Hundreds of thousands of instances of new malware arise every day. Waiting a year before you train people again can result in missed opportunities to stop new cyberattack methods.
Continuous training doesn’t have to mean lengthy, sit-down sessions. It can involve regular notifications of new threats, pop quizzes or simulated phishing attacks to keep employees vigilant. What is important is the regular exposure to help keep your employees on the lookout for that email that ”just doesn’t seem right.”
Zero Trust network methodology (with default deny policies) – Traditional security models have long assumed that anything inside a network could be trusted. Zero Trust, on the other hand, is exactly what it says — an approach that trusts nothing. Bad actors can easily disguise themselves as legitimate network users or exploit legitimate business resources. Trust the wrong person only once, and it can result in a devastating cyberattack.
Instead, this methodology emphasizes verification. One of the most common Zero Trust tools is multi-factor authentication. This is when confirming user identity requires two or more pieces of evidence. For example, an employee enters their user ID and password to log into their laptop (and your network). But instead of granting access right away, the system sends a push notification to the user’s cellphone. This notification might ask the user to approve the login or give them a code to enter on their laptop.
Advanced application control – Application controls prevent unauthorized applications from causing harm on your network. Once a bad actor get into your network (whether from a stolen password or an exploited vulnerability from an unpatched system), they will try to disable your safeguards, make their own administrator accounts and install more tools. These steps help them maintain their foothold, allowing them to do more damage. They often use common everyday tools in attacks, such as Microsoft Office macros, PowerShell, and even the ability to access files and run commands from inside the business applications.
Traditional security measures do not protect the applications from being misused. But with an advanced application control (AAC) solution, you can prevent an Office macro from accessing the internet or your line of business applications from launching PowerShell with elevated permissions. With an AAC you significantly restrict their ability to do harm.
Advanced file level security outside of the domain infrastructure – Much like an AAC does for applications, advanced file security (AFS) allows you to control access to specific sets of data outside of the standard Active Directory permissions. This too helps protect your business by minimizing the damage in the event a bad actor gets into your network.
If you have a smaller business that isn’t running Active Directory, restricting access to your information is just as critical to protect you from attacks such as ransomware. With AFS you can add additional protection that you otherwise wouldn’t have.
Direct alerts for administrative functions – All the technology you can employ to protect your business is still not enough. Someone needs to be looking for malicious activity.
Many tools mentioned above have the ability to report back when something happens. Microsoft Windows can alert when someone exercises a privilege such as creating or removing user accounts, elevating a user’s permissions to be an administrator or other actions that occur on a business network. Unfortunately, this is another area a bad actor will abuse if they get past your defenses.
Monitoring this activity can be a full-time job. But if you configure alerting from each of these systems to report when something happens, you can develop a baseline and look for trends or anomalies. This can ease some of the administrative burden inherent with solid security.
Simply put… If you’re not monitoring your alerts, you’ll be at the mercy of whatever happens.
The Best of Both Worlds
As we mentioned, the traditional methods of cyberattack prevention are anything but obsolete. That’s why combining them with newer tactics is the best way to safeguard your organization.
Imagine each method is a layer protecting your business. As you can see from the graphic below, user education is your front line of defense. Meanwhile, data backup retrieval and a business continuity plan are your last measures in the face of a successful attack.
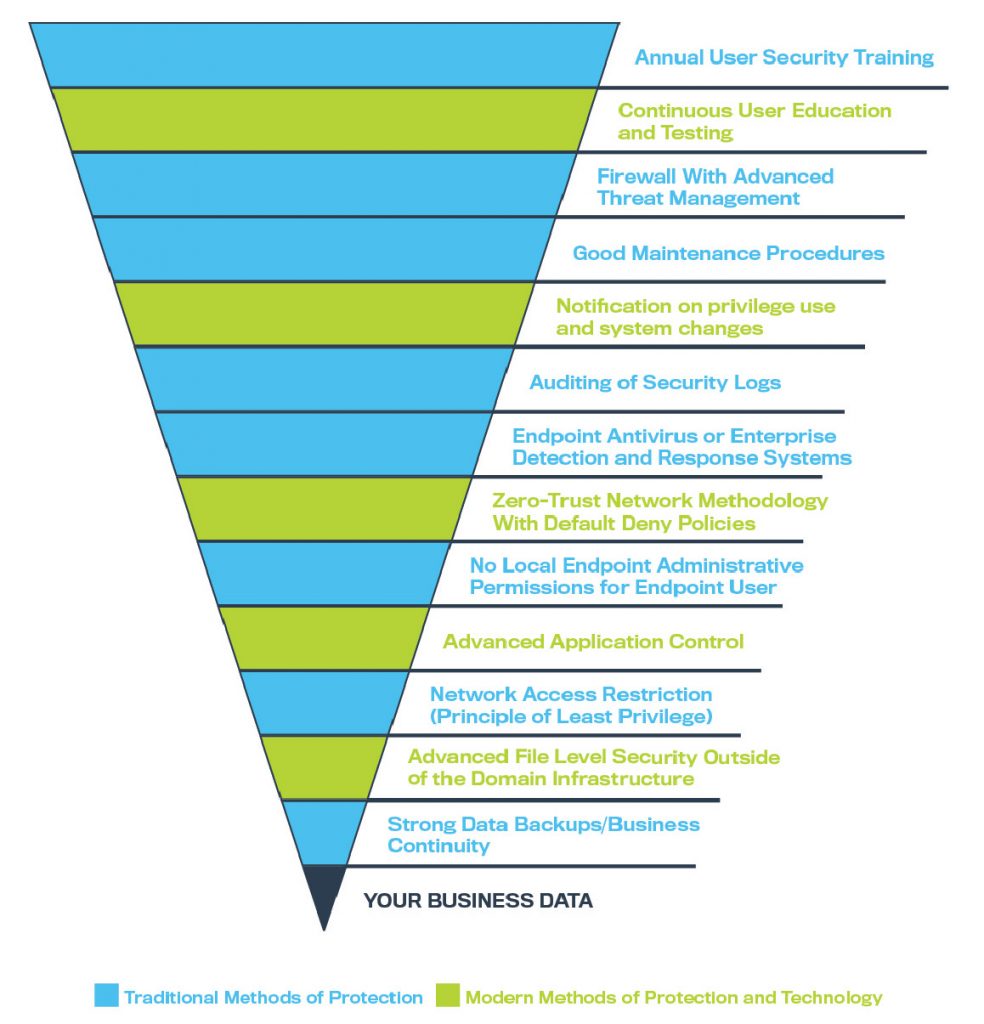
This order is an example of which tools to use and where they might fall in the hierarchy of prevention. That said, you should tailor your cyberattack defenses to the unique needs of your business. A seasoned technology consulting firm can help you weigh these options to see what would serve your needs best.




